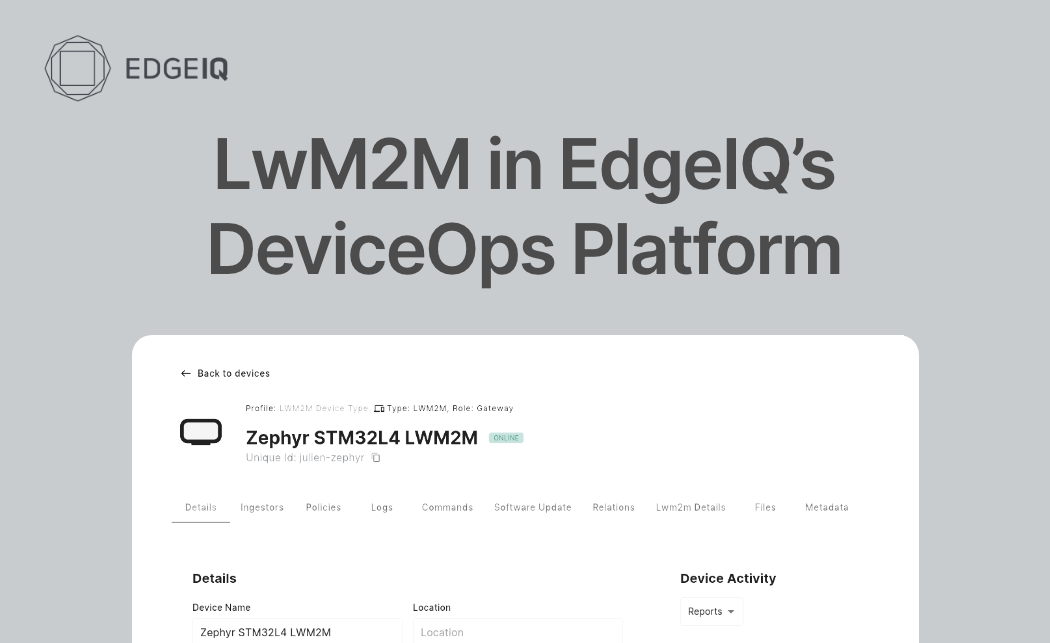
EdgelQ, a leading provider of DeviceOps solutions for the connected product economy, is excited to announce the integration of the Lightweight M2M (LwM2M) protocol into our product suite. As a technical standard developed by the Open Mobile Alliance (OMA), LwM2M addresses the unique requirements of managing low-power, constrained devices in the Internet of Things (loT) ecosystem. This introduction will provide an overview of LwM2M, its key features, and the benefits of using this standard protocol for managing your connected devices.
What is Lightweight M2M (LwM2M)?
Lightweight M2M is a device management protocol that offers a simple, efficient, and secure way to manage loT devices. It is built on top of the Constrained Application Protocol (CoAP), a specialized transfer protocol for use with constrained nodes and networks. LwM2M provides a lightweight, low-power solution for managing constrained devices, enabling seamless device-to-server communication.
Key Features of LwM2M
-
Low power consumption: LwM2M is designed to minimize power consumption, making it an ideal choice for battery-powered devices or those with limited energy resources.
-
Compact data representation: LwM2M uses a binary data format, reducing the payload size and enabling efficient communication over bandwidth-constrained networks.
-
Easy integration: LwM2M supports various communication transports, including cellular, Wi-Fi, and low-power wide-area networks (LPWANs), simplifying integration with existing networks.
-
Object-oriented model: LwM2M uses a flexible, object-oriented data model, allowing for easy customization and extensibility to accommodate various device types and requirements.
-
Built-in security: LwM2M includes built-in security mechanisms, such as Datagram Transport Layer Security (DTLS), to ensure secure communication between devices and servers
While LWM2M is an excellent choice for managing constrained devices, our EdgeIQ edge agent provides more advanced features and capabilities for Linux thick-edge devices. However, for thin-edge microcontrollers, LWM2M is the perfect choice for device management.
Registration and security key management phase
The bootstrapping phase in LwM2M is the initial phase where a device requests configuration data from a Bootstrap Server to establish a secure connection with the LWM2M Server. The bootstrap process typically occurs when a new device is added to the network or needs to be reconfigured.
During the bootstrap phase, the following steps occur:
-
Device requests bootstrap information: The device sends a bootstrap request to the Bootstrap Server, requesting information necessary to connect to the LWM2M Server. The bootstrap request typically includes information about the device identity and is made with factory-provided keys.
-
Bootstrap Server provides configuration data: This typically includes information such as the LWM2M Server's URL, security credentials, and other relevant information like the communication frequency.
-
Device stores configuration data: The device stores the configuration data received from the Bootstrap Server. This data is necessary to establish a secure connection with the LWM2M Server.
-
Device connects to LWM2M Server: Once the device has received the necessary configuration data, it can connect to the LWM2M Server and register with the server.
-
Re-Bootstrap process: In LWM2M, key rotation is achieved by triggering a re-bootstrap process. The device can trigger the rebootstrap process when it detects that it has lost connectivity with the LWM2M Server or experiencing repeated authentication failures. The re-bootstrap process involves the device requesting new security credentials from the Bootstrap Server.
Once successfully registered with the Lwm2m server, the device must update the registration following the frequency (lifetime) provided during the bootstrap configuration.
Device Management and Service Enablement phase
After the registration phase, the LwM2M server can interact with the LwM2M client to perform various operations, such as read, write, execute, and observe. These operations enable remote management of the client device.
1. Read: The read operation allows the LwM2M server to request the current value of a resource or an object instance from the LwM
For example, the server might request the current temperature reading from a temperature sensor. Server sends a READ request on the path "/3303/0/5700" which mean the Resource ID 5700 (Sensor Value) in the Temperature Object (Object ID 3303, Instance ID 0). Client responds with the current temperature value.
2. Write: The write operation enables the LwM2M server to update the value of a resource or an object instance on the LwM2M client.
For example, the server might update the desired temperature setpoint for a thermostat.
Server sends a WRITE request on the path "/3308/0/5900" to update Resource ID 5900 (Setpoint Value) in the Thermostat Object (Object ID 3308, Instance ID 0) with a new temperature setpoint.
Client updates the setpoint value accordingly.
3. Execute: The execute operation allows the LwM2M server to trigger a specific action on the LwM2M client by invoking an executable resource.
For example, the server might command a connected device to reboot or reset.
Server sends an EXECUTE request for Resource ID 4 (Reboot) in the Device Object (Object ID 3, Instance ID 0). Client performs the reboot action as requested.
4. Observe: The observe operation enables the LwM2M server to subscribe to changes in the value of a resource or an object instance on the LwM2M client. When the observed value changes, the client sends a notification to the server.
For example, the server might observe the battery level of a device and receive notifications when the battery level changes.
Server sends an OBSERVE request on the path "/3/0/9" for Resource ID 9 (Battery Level) in the Battery Object (Object ID 3, Instance ID 0).
Client acknowledges the request, and when the battery level changes, it sends a notification with the updated value to the server.
These operations facilitate flexible remote management and control of the client device, allowing the LwM2M server to interact with the client and perform necessary actions based on specific use cases and requirements.
Constrained Devices are better with DeviceOps
Cloud-based automation can significantly augment the capabilities of constrained microcontroller-based devices by providing additional features and flexibility in managing the devices remotely. For example, our DeviceOps capabilities can upgrade the firmware when an old version is detected or reconfigure devices that have drifted from their intended configurations.
For example, let's say that a fleet of temperature sensors has been deployed in a large region. Over time, the calibration settings on these sensors drift, leading to erroneous values. The cloud can detect the value and take some automatic measures: send an alert to an operator, read the firmware value, and send a new firmware if the value is incorrect, or resend the calibration parameters to the faulty device.
In this case, DeviceOps helps to reduce manual intervention and remove the need to implement those processes in a device already constrained by all the communication and security implementation mandated by modern IoT standards.
In conclusion, EdgelQ's Lightweight M2M protocol integration into our DeviceOps solution enables businesses to manage, maintain, and secure their connected devices efficiently. By adopting this industry-standard protocol, in combination with EdgeIQ DeviceOps capabilities, organizations use our flexible cloud-based automation to augment the capabilities of their constrained devices.
EdgeIQ is an API-first distributed software platform that provides the infrastructure to manage and integrate virtually any connected product and its data into business operations, infrastructure and customer ecosystems. EdgeIQ provides feature-rich, configurable device management, remote monitoring and orchestration software so that your organization can focus on building innovative and engaging data-driven products at a lower cost. Get started on your DeviceOps journey today